Configuring Redundancy using HSRP
Configuring Gateway load Balancing Protocol GLBP
Configuring Static and Dynamic NAT
Configuring Access Control Lists (ACLs)
Configuring Port Security
Configuring Inter-VLAN Routing
Configuring DHCP on Router
Full_CCNA_Course_With_Labs
WAN( config)# interface Loopback1 WAN( config-if)# ip address 200.200.200.1 255.255.255.0 WAN( config-if)# no shutdown WAN( config-if)# exit WAN( config)# interface Fa0/ 0 WAN( config-if)# ip address 172.16.2.1 255.255.255.0 WAN( config-if)# no shutdown WAN( config-if)# exit WAN( config)# interface Fa0/ 1 WAN( config-if)# ip address 172.16.1.1 255.255.255.0 WAN( config-if)# no shutdown WAN( config-if)# exit
WAN( config)# router rip WAN( config-router)# version 2 WAN( config-router)# network 172.16.1.0 WAN( config-router)# network 172.16.2.0 WAN( config-router)# network 200.200.200.0 WAN( config-router)# no auto-summary WAN( config-router)# exit
4. The following figure displays the RIP version 2 routing on WAN router.
5. Once you have configured IP addresses and routing on WAN router, move on to Master router and execute the following commands. This router will act as Active router.
6. Execute the following commands to configure IP address on the Fa0/ 0 interface.
Master( config)# interface Fa0/ 0 Master( config-if)# ip address 10.0.0.10 255.255.255.0 Master( config-if)# no shutdown Master( config-if)# exit
Master( config-if)# standby 1 ip 10.0.0.150
8. Next, execute the following command to set the priority value, preempt, and track interface.
Master( config-if)# standby 1 priority 101 Master( config-if)# standby 1 preempt Master( config-if)# standby 1 track fa0/ 1
Master( config)# interface Fa0/ 1 Master( config-if)# ip address 172.16.1.2 255.255.255.0 Master( config-if)# no shutdown Master( config-if)# exit
Master( config)# router rip Master( config-router)# version 2 Master( config-router)# network 172.16.1.0 Master( config-router)# network 10.0.0.0 Master( config-router)# no auto-summary Master( config-router)# exit
Backup( config)# interface Fa0/ 0 Backup( config-if)# ip address 10.0.0.20 255.255.255.0 Backup( config-if)# no shutdown Backup( config-if)# standby 1 ip 10.0.0.150 Backup( config-if)# standby 1 priority 99 Backup( config-if)# standby 1 preempt Backup( config-if)# exit Backup( config)# interface Fa0/ 1 Backup( config-if)# ip address 172.16.2.2 255.255.255.0 Backup( config-if)# no shutdown Backup( config-if)# exit Backup( config)# router rip Backup( config-router)# version 2 Backup( config-router)# network 172.16.2.0 Backup( config-router)# network 10.0.0.0 Backup( config-router)# no auto-summary Backup( config-router)# exit
14. In the preceding figure, you can see that Master router is currently working as Active router because it has higher priority (101) than Backup router (99).
Master( config)# int fa0/ 0 Master( config-if)# shutdown
Backup# show standby
17. In the preceding figure you can see that Backup router becomes the Active router and takes the routing responsibilities as soon as the interface of Master router goes down. This is what does a redundancy protocol.
Configuring Gateway load Balancing Protocol GLBP
LABS:
The AVG's mission is to distribute the load between the different gateways (itself and the different AVF). To achieve this, he will be responsible for responding to ARP requests by varying the response, indicating his own, that of an AVF, that of the next AVF etc.
Configuration on R1
R1(config)#interface FastEthernet 0/0 R1(config-if)#glbp 10 ip 10.0.0.254 R1(config-if)#glbp 10 preempt R1(config-if)#glbp 10 priority 150 *Mar 1 00:27:32.447: %GLBP-6-STATECHANGE: FastEthernet0/0 Grp 10 state Standby -> Active *Mar 1 00:27:42.451: %GLBP-6-FWDSTATECHANGE: FastEthernet0/0 Grp 10 Fwd 1 stat
FastEthernet0/0 - Group 10
State is Active
2 state changes, last state change 00:04:25
Virtual IP address is 10.0.0.254
Hello time 3 sec, hold time 10 sec
Next hello sent in 1.052 secs
Redirect time 600 sec, forwarder timeout 14400 sec
Preemption enabled, min delay 0 sec
Active is local
Standby is unknown
Priority 150 (configured)
Weighting 100 (default 100), thresholds: lower 1, upper 100
Load balancing: round-robin
Group members:
c000.116c.0000 (10.0.0.1) local <== MAC réelle
There is 1 forwarder (1 active)
Forwarder 1
State is Active
1 state change, last state change 00:04:15
MAC address is 0007.b400.0a01 (default) <== MAC Virtuelle
Owner ID is c000.116c.0000
Redirection enabled
Preemption enabled, min delay 30 sec
Active is local, weighting 100
Configuration on R2
R2(config)#int FastEthernet 0/0 R2(config-if)#glbp 10 ip 10.0.0.254
R2#show glbp
FastEthernet0/0 - Group 10
State is Standby
1 state change, last state change 00:01:55
Virtual IP address is 10.0.0.254
Hello time 3 sec, hold time 10 sec
Next hello sent in 1.120 secs
Redirect time 600 sec, forwarder timeout 14400 sec
Preemption disabled
Active is 10.0.0.1, priority 150 (expires in 8.380 sec)
Standby is local
Priority 100 (default)
Weighting 100 (default 100), thresholds: lower 1, upper 100
Load balancing: round-robin
Group members:
c000.116c.0000 (10.0.0.1)
c001.116c.0000 (10.0.0.2) local
There are 2 forwarders (1 active)
Forwarder 1
State is Listen
MAC address is 0007.b400.0a01 (learnt)
Owner ID is c000.116c.0000
Time to live: 14398.376 sec (maximum 14400 sec)
Preemption enabled, min delay 30 sec
Active is 10.0.0.1 (primary), weighting 100 (expires in 9.192 sec)
Forwarder 2
State is Active
1 state change, last state change 00:02:05
MAC address is 0007.b400.0a02 (default)
Owner ID is c001.116c.0000
Preemption enabled, min delay 30 sec
Active is local, weighting 100VERIFY
C1#ping 1.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 1.1.1.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 8/21/48 ms
C1#show arp
Protocol Address Age (min) Hardware Addr Type Interface
Internet 10.0.0.254 2 0007.b400.0a01 ARPA FastEthernet0/0
C1#C2#ping 1.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 1.1.1.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 8/25/40 ms
C2#show arp
Protocol Address Age (min) Hardware Addr Type Interface
Internet 10.0.0.254 1 0007.b400.0a02 ARPA FastEthernet0/0
C2#Configuring Static and Dynamic NAT
Configure Static NAT
To configure NAT, you need to perform the following steps:
1. On Router1, execute the following command to specify the inside interface that is Fa0/ 0.
Router1( config)# int fa0/ 0 Router1( config-if)# ip nat inside Router1( config-if)# exit
2. Next, execute the following command to specify the outside interface that is Fa0/ 1.
Router1( config)# int fa0/ 1 Router1( config-if)# ip nat outside Router1( config-if)# exit
3. Once you have defined the inside and outside interfaces, now you need to specify the private IP addresses that need to be translated into the public IP addresses. In this demonstration, we will translate 10.0.0.2 private IP address into the 200.200.200.1 public IP address. To do so, execute the following command.
Router1( config)# ip nat inside source static 10.0.0.2 200.200.200.1 Router1( config)# exit
4. The following figure shows how to configure static NAT on a router.
5. Once you have configured static NAT, now it’s time to verify your configuration. To verify the static NAT configuration, start a communication process between inside and outside networks. For this, open the Command Prompt window on PC0 and type ping 20.0.0.2. Leave the Command Prompt active and move on to Router1.
6. On Router1, type the following command to view the NAT translation table.
Router1# show ip nat translations
7. In the preceding figure, you can see that 10.0.0.2 private IP address has been translated into 200.200.200.1 public IP address. That’s what does NAT actually.
Removing NAT Configuration
If you have mapped a wrong IP address or want to disable the NAT translation for any reason, execute the following command.
Router1( config)# no ip nat inside source static 10.0.0.2 200.200.200.1
Now, your topology is ready to perform the next exercise “configure dynamic NAT”. If you have doubts on topology, better to reload the topology and re-configure the IP addresses and routing method.
Configure Dynamic NAT
As discussed earlier, dynamic NAT is used for a large network or when a large number of users want to access external resources. Configuring dynamic NAT is slightly different from the static NAT. In dynamic NAT, you need to apply an ACL to specify which users or networks are allowed to access external resources and need to be translated. After that you need to create a Range of IP addresses (pool) from which the NAT router will allocate the IP addresses to internal users on the first come first serve basis.
To configure dynamic NAT, you need to perform the following steps:
1. On Router1, execute the following commands to specify the inside and outside interfaces.
Router1( config)# int fa0/ 0 Router1( config-if)# ip nat inside Router1( config-if)# exit Router1( config)# int fa0/ 1 Router1( config-if)# ip nat outside Router1( config-if)# exit
2. Now, execute the following command to create a pool and specify the ranges that the NAT router will use to allocate IP addresses.
Router1( config)# ip nat pool mypool 150.150.1.1 150.150.1.10 netmask 255.255.0.0
3. Next, execute the following command to apply the created pool.
Router1( config)# ip nat inside source list 10 pool mypool
4. Next, execute the following commands to apply an ACL to allow the networks.
Router1( config)# access-list 10 permit 10.0.0.0 0.255.255.255
5. Next, execute the following command to specify the interface and the ACL direction.
Router1( config)# int fa0/ 0
6. Router1( config-if)# ip access-group 50 out
Router1( config-if)# exit Router1( config)# exit
7. The following figure shows the Dynamic NAT configuration on Router1.
Configuring Static and Dynamic NAT
Network Address Translation (NAT) technique translates private IP addresses into public IP addresses. NAT enhances the security of the network by hiding the actual IP information from the external users. The external users see the translated IP addresses rather than actual IP addresses. This is also called masking. There are two types of NAT: Static NAT and Dynamic NAT.
The Static NAT is useful for a small number of users where an administrator can manually create a MAP table of Public and Private IP addresses. However, for a large network where the number of users are in hundreds and thousands, it is not possible or at least a difficult task to create a MAP table manually. Here, you can use Dynamic NAT that allows you to define a range of public IP addresses that will be translated. When the internal users (inside network) try to access external resources (outside network), the NAT router replaces its private IP address with the available Public IP address from the configured range.
We will use the following topology to demonstrate how to configure NAT. Create the following topology in Cisco Packet Tracer.

After creating the preceding topology, configure the appropriate IP addresses on the devices mentioned in the topology. In addition, you also need to perform a routing algorithm. You can use any of the routing algorithms depending on your choice. So before proceed to next prepare your topology.
Configure Static NAT
To configure NAT, you need to perform the following steps:
1. On Router1, execute the following command to specify the inside interface that is Fa0/ 0.
Router1( config)# int fa0/ 0 Router1( config-if)# ip nat inside Router1( config-if)# exit
2. Next, execute the following command to specify the outside interface that is Fa0/ 1.
Router1( config)# int fa0/ 1 Router1( config-if)# ip nat outside Router1( config-if)# exit
3. Once you have defined the inside and outside interfaces, now you need to specify the private IP addresses that need to be translated into the public IP addresses. In this demonstration, we will translate 10.0.0.2 private IP address into the 200.200.200.1 public IP address. To do so, execute the following command.
Router1( config)# ip nat inside source static 10.0.0.2 200.200.200.1 Router1( config)# exit
4. The following figure shows how to configure static NAT on a router.

5. Once you have configured static NAT, now it’s time to verify your configuration. To verify the static NAT configuration, start a communication process between inside and outside networks. For this, open the Command Prompt window on PC0 and type ping 20.0.0.2. Leave the Command Prompt active and move on to Router1.
6. On Router1, type the following command to view the NAT translation table.
Router1# show ip nat translations

7. In the preceding figure, you can see that 10.0.0.2 private IP address has been translated into 200.200.200.1 public IP address. That’s what does NAT actually.
Removing NAT Configuration
If you have mapped a wrong IP address or want to disable the NAT translation for any reason, execute the following command.
Router1( config)# no ip nat inside source static 10.0.0.2 200.200.200.1
Now, your topology is ready to perform the next exercise “configure dynamic NAT”. If you have doubts on topology, better to reload the topology and re-configure the IP addresses and routing method.
Configure Dynamic NAT
As discussed earlier, dynamic NAT is used for a large network or when a large number of users want to access external resources. Configuring dynamic NAT is slightly different from the static NAT. In dynamic NAT, you need to apply an ACL to specify which users or networks are allowed to access external resources and need to be translated. After that you need to create a Range of IP addresses (pool) from which the NAT router will allocate the IP addresses to internal users on the first come first serve basis.
To configure dynamic NAT, you need to perform the following steps:
1. On Router1, execute the following commands to specify the inside and outside interfaces.
Router1( config)# int fa0/ 0 Router1( config-if)# ip nat inside Router1( config-if)# exit Router1( config)# int fa0/ 1 Router1( config-if)# ip nat outside Router1( config-if)# exit
2. Now, execute the following command to create a pool and specify the ranges that the NAT router will use to allocate IP addresses.
Router1( config)# ip nat pool mypool 150.150.1.1 150.150.1.10 netmask 255.255.0.0
3. Next, execute the following command to apply the created pool.
Router1( config)# ip nat inside source list 10 pool mypool
4. Next, execute the following commands to apply an ACL to allow the networks.
Router1( config)# access-list 10 permit 10.0.0.0 0.255.255.255
5. Next, execute the following command to specify the interface and the ACL direction.
Router1( config)# int fa0/ 0
6. Router1( config-if)# ip access-group 50 out
Router1( config-if)# exit Router1( config)# exit
7. The following figure shows the Dynamic NAT configuration on Router1.

Verify Dynamic NAT configuration
1. To verify dynamic NAT configuration, open command prompts on PC0 and PC1 and type the following command on both PCs:
Ping 192.168.1.2
2. Now, execute the following command to show the translated IP addresses.
Router1# show ip nat translations
3. Close the Cisco Packet Tracer.
Configuring Access Control Lists (ACLs)
Types of ACL
An ACL can be either of the following two types.
Standard access lists
A Standard access list can use only the source IP address in an IP packet to filter the network traffic. Standard access lists are typically used permit or deny an entire system or network. They cannot be used to filter individual protocol or services such as FTP and Telnet.
Extended access lists
Extended access lists use the source and destination IP addresses. They can be used to filter specific protocol or service.
An ACL can be configured using either a number or a name. If you decide to use a name to configure an ACL it is referred as Named ACL.
Let’s see how to configure ACL
1. We will use the following topology to configure ACL. Create the following topology in Cisco Packet Tracer.
Configuring Access Control Lists (ACLs)
Access Control List (ACL) is a security feature that allows you to filter the network traffic based on configured statements. An ACL can be used to filter either inbound or outbound traffic on an interface. Once you applied an access list on a router, the router examine every packet moving from interface to another interface in the specified direction and takes the appropriate action.
Types of ACL
An ACL can be either of the following two types.
Standard access lists
A Standard access list can use only the source IP address in an IP packet to filter the network traffic. Standard access lists are typically used permit or deny an entire system or network. They cannot be used to filter individual protocol or services such as FTP and Telnet.
Extended access lists
Extended access lists use the source and destination IP addresses. They can be used to filter specific protocol or service.
An ACL can be configured using either a number or a name. If you decide to use a name to configure an ACL it is referred as Named ACL.
Let’s see how to configure ACL
1. We will use the following topology to configure ACL. Create the following topology in Cisco Packet Tracer.

2. Once you have created the preceding topology, configure the appropriate IP addresses as mentioned in the topology. To do so, execute the following commands on Router1.
Router1( config)# int fa0/ 0 Router1( config-if)# ip add 10.0.0.1 255.0.0.0 Router1( config-if)# no shut Router1( config-if)# exit Router1( config)# int fa0/ 1 Router1( config-if)# ip add 192.168.0.1 255.255.255.0 Router1( config-if)# no shut Router1( config-if)# exit
3. Once you have configured appropriate IP addresses, use a routing method such as RIP. To do so, execute the following commands on Router1.
Router1( config)# router rip Router1( config-router)# network 192.168.0.0 Router1( config-router)# network 10.0.0.0 Router1( config-router)# exit Router1( config)#
4. Next, move on to Router2 and execute the following commands to configure IP addresses and the RIP routing protocol.
Router2( config)# int fa0/ 0 Router2( config-if)# ip add 20.0.0.1 255.0.0.0 Router2( config-if)# no shut Router2( config-if)# exit Router2( config)# int fa0/ 1 Router2( config-if)# ip add 192.168.0.2 255.255.255.0 Router2( config-if)# no shut Router2( config-if)# exit Router2( config)# router rip Router2( config-router)# network 192.168.0.0 Router2( config-router)# network 20.0.0.0 Router2( config-router)# exit
5. After configuring IP addresses on routers, configure IP addresses on PC0, PC1, and Server.
6. Now, open the Command Prompt on PC0 and type ping 20.0.0.2 you should be able to ping successfully. Save the topology as it will be used to demonstrate the next exercises.
Now, you have configured the appropriate IP addresses and routing on your network topology. Before configuring an ACL, we would like to explain the command syntaxes used to configure it. As discussed earlier you either use the numbered ACL method or Named ACL method.
7. The following figure shows the command syntax used to configure an ACL.
Configure Standard ACL
Let’s see how to configure Standard ACL. In this demonstration, we will restrict host 10.0.0.2 from accessing Router2. To do so, perform the following steps:
1. First, execute the following command to deny host 10.0.0.2.
Router2( config)# access-list 10 deny host 10.0.0.2
2. Once you deny a host on a router, the router will deny all the hosts until you explicitly define the permitted hosts. In the following command we will permit all the hosts.
Router2( config)# access-list 10 permit any
3. Next, switch to the interface on which you want to apply the ACL, in this case Fa0/ 1, and define the direction (inbound or outbound) of traffic that you want to filter. In this case, we will filter the incoming packets towards Router2. To do so execute the following commands.
Router2( config)# int fa0/ 1 Router2( config-if)# ip access-group 10 in Router2( config-if)# exit Router2( config)# exit
4. Once you applied an ACL on a router, execute the following command to view the applied ACLs.
Router2# show ip access-lists
6. Now, you have tested your ACL configuration. Now, remove the ACL configuration so the next exercise could be performed. To remove the configured ACL, execute the following command on Router2.
Router2( config)# no access-list 10 deny host 10.0.0.2
7. Try to ping again from PC0 to Router2, this time you should be able ping successfully, because you have removed the applied ACL.
Configure Extended ACL.
In the previous exercise, we have discussed the basics of Access Control Lists (ACLs) and how to configure standard ACL. In this exercise, we will explain how to configure Extended ACL on Cisco routers. We assume that you have loaded the previous topology and the standard ACL configuration are removed.
Syntax to configure an Extended ACL.
1. Once you have done the TCP/ IP and routing configuration, let’s have a look at the syntax used to configure an Extended ACL on Cisco routers.
Router( config)# access-list < an ACL number from 100-199 > < select an action > < select a protocol or service > < source address > < destination address > < port number > < packet condition >
2. If the preceding syntax does not help you, let’s have a look at the syntax in detail. The following figure shows the syntax to select the action, protocol, and source address.
Let’s begin the configuration
To configure Extended Access Control List, we will use the following network topology. In this example, we will deny the host 10.0.0.2 from accessing the Web server (20.0.0.2).
1. In order to prevent host 10.0.0.2 to access the Web server (20.0.0.2), you need to execute the following commands.
Router2( config)# access-list 150 deny tcp host 10.0.0.2 host 20.0.0.2 0.0.0.0 eq www Router2( config)# access-list 150 permit ip any any Router2( config)# int fa0/ 1 Router2( config-if)# ip access-group 150 in Router2( config-if)# exit Router2( config)# exit
2. Once you applied an ACL on the desired interface, execute the following command to view the configured access lists.
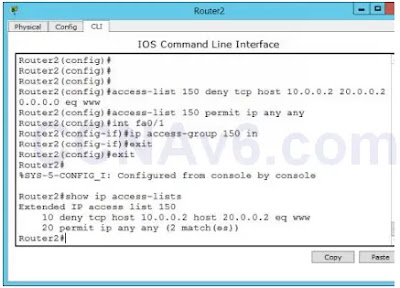
Router2# show ip access-lists
3. The following figure shows how to configure an extended ACL on cisco router.
Verify Access Control List Configuration.
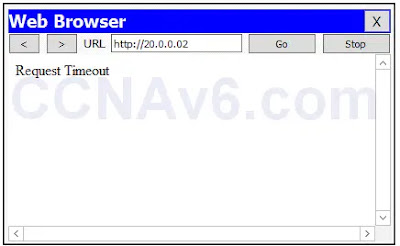
1. To verify your configuration, open the Web browser on PC0, type http:// 20.0.0.2 and press Enter. You should not be able to access the Web server, as shown in the following figure.
Configuring Access Control Lists (ACLs)
Access Control List (ACL) is a security feature that allows you to filter the network traffic based on configured statements. An ACL can be used to filter either inbound or outbound traffic on an interface. Once you applied an access list on a router, the router examine every packet moving from interface to another interface in the specified direction and takes the appropriate action.
Types of ACL
An ACL can be either of the following two types.
Standard access lists
A Standard access list can use only the source IP address in an IP packet to filter the network traffic. Standard access lists are typically used permit or deny an entire system or network. They cannot be used to filter individual protocol or services such as FTP and Telnet.
Extended access lists
Extended access lists use the source and destination IP addresses. They can be used to filter specific protocol or service.
An ACL can be configured using either a number or a name. If you decide to use a name to configure an ACL it is referred as Named ACL.
Let’s see how to configure ACL
1. We will use the following topology to configure ACL. Create the following topology in Cisco Packet Tracer.

2. Once you have created the preceding topology, configure the appropriate IP addresses as mentioned in the topology. To do so, execute the following commands on Router1.
Router1( config)# int fa0/ 0 Router1( config-if)# ip add 10.0.0.1 255.0.0.0 Router1( config-if)# no shut Router1( config-if)# exit Router1( config)# int fa0/ 1 Router1( config-if)# ip add 192.168.0.1 255.255.255.0 Router1( config-if)# no shut Router1( config-if)# exit
3. Once you have configured appropriate IP addresses, use a routing method such as RIP. To do so, execute the following commands on Router1.
Router1( config)# router rip Router1( config-router)# network 192.168.0.0 Router1( config-router)# network 10.0.0.0 Router1( config-router)# exit Router1( config)#
4. Next, move on to Router2 and execute the following commands to configure IP addresses and the RIP routing protocol.
Router2( config)# int fa0/ 0 Router2( config-if)# ip add 20.0.0.1 255.0.0.0 Router2( config-if)# no shut Router2( config-if)# exit Router2( config)# int fa0/ 1 Router2( config-if)# ip add 192.168.0.2 255.255.255.0 Router2( config-if)# no shut Router2( config-if)# exit Router2( config)# router rip Router2( config-router)# network 192.168.0.0 Router2( config-router)# network 20.0.0.0 Router2( config-router)# exit
5. After configuring IP addresses on routers, configure IP addresses on PC0, PC1, and Server.
6. Now, open the Command Prompt on PC0 and type ping 20.0.0.2 you should be able to ping successfully. Save the topology as it will be used to demonstrate the next exercises.
Now, you have configured the appropriate IP addresses and routing on your network topology. Before configuring an ACL, we would like to explain the command syntaxes used to configure it. As discussed earlier you either use the numbered ACL method or Named ACL method.
7. The following figure shows the command syntax used to configure an ACL.

Configure Standard ACL
Let’s see how to configure Standard ACL. In this demonstration, we will restrict host 10.0.0.2 from accessing Router2. To do so, perform the following steps:
1. First, execute the following command to deny host 10.0.0.2.
Router2( config)# access-list 10 deny host 10.0.0.2
2. Once you deny a host on a router, the router will deny all the hosts until you explicitly define the permitted hosts. In the following command we will permit all the hosts.
Router2( config)# access-list 10 permit any
3. Next, switch to the interface on which you want to apply the ACL, in this case Fa0/ 1, and define the direction (inbound or outbound) of traffic that you want to filter. In this case, we will filter the incoming packets towards Router2. To do so execute the following commands.
Router2( config)# int fa0/ 1 Router2( config-if)# ip access-group 10 in Router2( config-if)# exit Router2( config)# exit
4. Once you applied an ACL on a router, execute the following command to view the applied ACLs.
Router2# show ip access-lists

5. Next, open the Command Prompt of PC0, try to ping 192.168.0.2, you should not be able to ping, as shown in the following figure.

6. Now, you have tested your ACL configuration. Now, remove the ACL configuration so the next exercise could be performed. To remove the configured ACL, execute the following command on Router2.
Router2( config)# no access-list 10 deny host 10.0.0.2
7. Try to ping again from PC0 to Router2, this time you should be able ping successfully, because you have removed the applied ACL.
Configure Extended ACL.
In the previous exercise, we have discussed the basics of Access Control Lists (ACLs) and how to configure standard ACL. In this exercise, we will explain how to configure Extended ACL on Cisco routers. We assume that you have loaded the previous topology and the standard ACL configuration are removed.
Syntax to configure an Extended ACL.
1. Once you have done the TCP/ IP and routing configuration, let’s have a look at the syntax used to configure an Extended ACL on Cisco routers.
Router( config)# access-list < an ACL number from 100-199 > < select an action > < select a protocol or service > < source address > < destination address > < port number > < packet condition >
2. If the preceding syntax does not help you, let’s have a look at the syntax in detail. The following figure shows the syntax to select the action, protocol, and source address.

3. The following figure shows the syntax to select the destination address and packet filter method.

4. The following figure shows the syntax to select the port number.

Let’s begin the configuration
To configure Extended Access Control List, we will use the following network topology. In this example, we will deny the host 10.0.0.2 from accessing the Web server (20.0.0.2).

1. In order to prevent host 10.0.0.2 to access the Web server (20.0.0.2), you need to execute the following commands.
Router2( config)# access-list 150 deny tcp host 10.0.0.2 host 20.0.0.2 0.0.0.0 eq www Router2( config)# access-list 150 permit ip any any Router2( config)# int fa0/ 1 Router2( config-if)# ip access-group 150 in Router2( config-if)# exit Router2( config)# exit
2. Once you applied an ACL on the desired interface, execute the following command to view the configured access lists.
Router2# show ip access-lists
3. The following figure shows how to configure an extended ACL on cisco router.

Verify Access Control List Configuration.
1. To verify your configuration, open the Web browser on PC0, type http:// 20.0.0.2 and press Enter. You should not be able to access the Web server, as shown in the following figure.

2. Now move on to PC2 and try to access Web server, this time you should be able to access Web server. This is because we have not prevented PC2 to access Web server.

3. Now, you have configured and verified the Extended ACL, you can remove the configured ACL. To do so, execute the following command on Router2.
Router2( config)# no access-list 150 deny tcp host 10.0.0.2 host 20.0.0.2 eq www
4. Close the Cisco Packet tracer.
Configuring Port Security
Configuration
We will use the following topology to configure switch port security. Create the following topology in Cisco Packet Tracer.
2. Next, switch to the interface on which you want to implement port security. For example interface Fa0/ 1.
Switch( config)# interface fa0/ 1
3. Next, execute the following commands to enable the access mode and port security feature.
Switch1( config-if)# switchport mode access Switch1( config-if)# switchport port-security
4. Next, execute the following commands to bind the MAC address that you want to allow to access this interface and to set the maximum number of MAC addresses to this interface.
Switch1( config-if)# switchport port-security mac-address 00D0. BC9A. 42DC Switch1( config-if)# switchport port-security maximum 1
5. Next, execute the following commands to set the violation policy and exit from the interface configuration mode.
Switch1( config-if)# switchport port-security violation shutdown Switch1( config-if)# exit Switch1( config)# exit
6. The following figure shows the port-security configuration options.
7. Next, execute the following command to show the MAC addresses associated with the interfaces, as shown in the following figure.
Switch# show port-security address
8. The following figure port-security configuration example.
9. Next, execute the following command to show the port security settings of the interface Fa0/ 1, as shown in the following figure.
Switch# show port-security interface 0/ 1
Configuring Inter-VLAN Routing
1. On the switch, execute the following commands to configure appropriate VLANs and assign appropriate interfaces to the respective VLANs.
Switch1( config)# vlan 10 Switch1( config-vlan)# name Sales Switch1( config-vlan)# exit
2. Once you have configured Sales VLAN, execute the following commands to assign the Fa0/ 1 interface to Sales VLAN.
Switch1( config)# interface fa0/ 1 Switch1( config-if)# switchport mode access Switch1( config-if)# switchport access vlan 10 Switch1( config-if)# exit
3. Execute the following commands to create another VLAN named Account with the VLAN ID as 20.
Switch1( config)# vlan 20 Switch1( config-vlan)# name Account Switch1( config-vlan)# exit
4. Once you have created Account VLAN, execute the following commands to assign the Fa0/ 2 interface to Account VLAN.
Switch1( config)# interface fa0/ 2 Switch1( config-if)# switchport mode access Switch1( config-if)# switchport access vlan 20 Switch1( config-if)# exit
5. Next, execute the following commands to enable VLAN trunking on the Fa0/ 3 interface.
Switch1( config)# interface fa0/ 3 Switch1( config-if)# switchport mode trunk Switch1( config-if)# exit
6. After configuring VLANs and VLAN trunking on switch, configure the following TCP/ IP settings on PC0:
- IP address: 10.0.0.1
- Subnet mask: 255.0.0.0
- Default gateway: 10.0.0.100
7. Next, configure the following TCP/ IP settings on PC1:
- IP address: 20.0.0.1
- Subnet mask: 255.0.0.0
- Default gateway: 20.0.0.100
8. Once you have configured appropriate TCP/ IP settings on PC0 and PC1, move to Router. On Router, execute the following command to enable its Fa0/ 0 interface.
Router( config)# interface fa0/ 0 Router( config-if)# no ip address Router( config-if)# no shutdown Router( config-if)# exit
9. On Router, execute the following commands to enable the dot1q encapsulation protocol (along with the VLAN ID) and to configure 10.0.0.100/ 8 IP address on its fa0/ 0.10 virtual sub-interface.
Router( config)# interface fa0/ 0.10 Router( config-subif)# encapsulation dot1q 10 Router( config-subif)# ip address 10.0.0.100 255.0.0.0 Router( config-subif)# exit
10. On Router, execute the following commands to enable the dot1q encapsulation protocol (along with the VLAN ID) and to configure 20.0.0.100/ 8 IP address on its fa0/ 0.20 virtual sub-interface.
Router( config)# interface fa0/ 0.20 Router( config-subif)# encapsulation dot1q 20 Router( config-subif)# ip address 20.0.0.100 255.0.0.0 Router( config-subif)# exit
11. Next, execute the following commands to configure the RIP routing (or any other depending on your choice) on Router.
Router( config)# router rip Router( config-router)# network 10.0.0.0 Router( config-router)# network 20.0.0.0 Router( config)# exit
12. The following figure displays the Inter-VLAN configuration on Router.
13. That’s all you need to configure for Inter-VLAN routing. Now, it’s time to verify your configuration. To do so, open Command Prompt on PC1, type the following commands to check the connectivity to PC0.
- Tracert 10.0.0.1
- Ping 10.0.0.1
14. You should be able to communicate to PC0 even both the PCs belong to different subnets and VLANs.
Configuring DHCP on Router
First, add the required devices in Cico Packet Tracer and connect them appropriatley. In the preceding topology, Router1 will act as DHCP server while Router2 and PC1 will act as DCHP clients. Let’s begin the exercise.
1. On Router1, execute the following commands to configure an IP address.
Router( config)# int fa0/ 0 Router( config-if)# ip add 10.0.0.1 255.0.0.0 Router( config-if)# no shut
2. Next, create a DHCP pool named DhcpPool1. Use 10.0.0.1 IP address as the default gateway and DNS server. Use 10.0.0.0 255.0.0.0 as network ID.
Router( config)# ip dhcp pool DhcpPool1 Router( dhcp-config)# default-router 10.0.0.1 Router( dhcp-config)# dns-server 10.0.0.1 Router( dhcp-config)# network 10.0.0.0 255.0.0.0 Router( dhcp-config)# exit
By default DHCP server will start to assign IP addresses from the first IP address of the assigned network ID and it will be 10.0.0.1/ 8. However, we have already configured this IP addresses manually on Fa0/ 0 interface of Router1. To avoid the confliction between DHCP assigned and manually assigned IP addresses, you can exclude one or more specific IP addresses or IP ranges from the DHCP pool. DHCP server will not distribute these IP addresses to any of the DHCP client.
3. The following commands will exclude 10.0.0.0.1 to 10.0.0.100 IP addresses that will not be distributed by DHCP server.
Router( config)# ip dhcp excluded-address 10.0.0.1 10.0.0.100 Router( config)# exit
4. On Router2, we will assign an IPv4 address on the Fa0/ 0 interface through the DHCP server. To do this, execute the following commands.
Router( config)# int fa0/ 0 Router( config-if)# ip add dhcp Router( config-if)# no shut
5. Wait for a few seconds and then execute the following command to view the IP address on Router2.
Router2# show ip int brief
or
Router2( config)# do show ip int brief
Note: Adding the do command before the show command allows you to execute privilege mode commands from the global configuration mode.
6. Once you have configured an IP address on Router2, switch to PC1, and try to obtain TCP/ IP settings through the DHCP server. To do so, open the console of PC1, select the Desktop tab. On the available options, click IP Configuration and then select the DHCP radio button.
7. After a few seconds, DHCP server will assign an IP address from the configured DHCP pool along with a default gateway and DNS server IP addresses.
8. In the preceding figure, you can see that 10.0.0.102 IP address has been assigned by the DHCP server.




































No comments:
Post a Comment